Week 17 - Session 2 - User Authentication - JSON Web Tokens
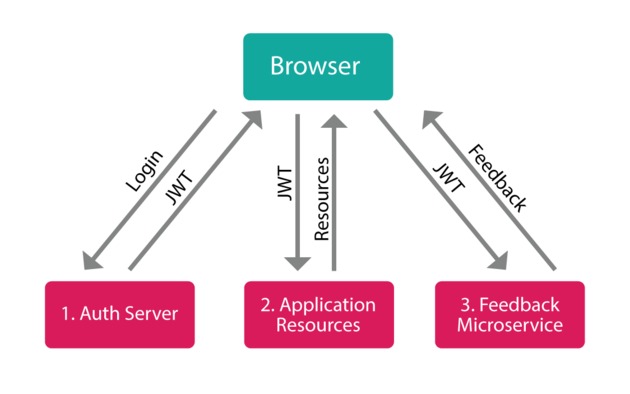 |
| blog image source |
JSON Web Token (JWT) Process:
- Encrypted string issued by the web server
- Stored by the client, typically in local storage
- Web server signs token using a SECRET KEY
- When the token is sent back to the server, can verify it using the secret key
- If the token is tampered with, verification will fail
- Header; consists of two parts: the type of the token, which is JWT, and the hashing algorithm.
- Payload; which contains the claims which are an entity (typically, the user) and additional metadata.
- Signature; takes the encoded header, the encoded payload, a secret, the algorithm specified in the header, and sign that.
5 Easy Steps to Understanding JSON Web Tokens (JWT) - https://medium.com/vandium-software/5-easy-steps-to-understanding-json-web-tokens-jwt-1164c0adfcec

